SCADA Security: Protecting Your Industrial Control Systems from Cyber Threats
Blog
4 Min Read
Supervisory Control and Data Acquisition (SCADA) systems are critical for controlling and monitoring industrial processes. SCADA systems are used in industries such as oil and gas, power generation, manufacturing, and water treatment. SCADA Systems are responsible for monitoring and controlling vital parameters, such as temperature, pressure, flow rates, and more. SCADA systems are often connected to other networks, which can create security vulnerabilities. It is essential to protect SCADA systems from cyber threats to ensure their reliable and secure operation.
In this blog post, we will discuss the importance of SCADA security and provide tips for protecting industrial control systems from cyber threats.
Why is SCADA Security Important?
SCADA systems control and monitor industrial processes that can have severe consequences if they fail. For example, a failure in a nuclear power plant’s SCADA system could lead to a catastrophic accident. SCADA systems are often connected to other networks, which can create security vulnerabilities. A successful cyber attack on a SCADA system could result in unauthorized access, data theft, or even sabotage of industrial processes.
SCADA systems are highly targeted by cybercriminals because of their criticality and the potential consequences of a successful attack. A SCADA system’s vulnerability can result in the theft of intellectual property, business disruption, and the compromise of industrial processes, leading to severe consequences.
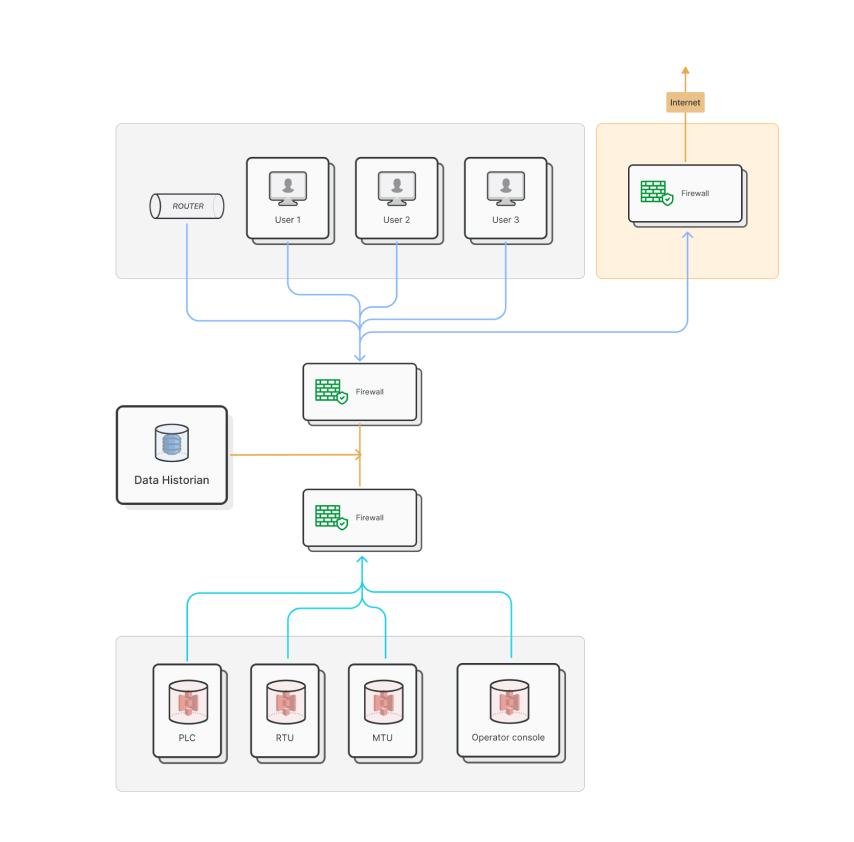
Protecting SCADA Systems from Cyber Threats
To protect SCADA systems from cyber threats, it is essential to implement appropriate security measures. Here are some tips for protecting industrial control systems from cyber threats:
- Secure Remote Access
One of the most significant vulnerabilities of SCADA systems is remote access. Remote access must be secured using two-factor authentication, firewalls, and encrypted communication channels. Limiting remote access to only those who require it is also essential. - Network Segmentation
Network segmentation is a critical strategy for protecting SCADA systems from cyber attacks. SCADA systems should be isolated from other networks to limit the impact of a cyber attack. Network segmentation can limit the impact of a successful cyber attack and prevent lateral movement within the network.Implementing best practices such as physical and logical segmentation, access control, network traffic monitoring, and regular review can help ensure that the SCADA network remains isolated and protected from cyber threats.
- Regular Patching and Updating
SCADA systems might be built using outdated software and hardware. Regular patching and updating of SCADA systems is essential for maintaining their security and reducing the risk of cyber attacks. If SCADA systems use outdated software and hardware, that can make the manufacturing facility vulnerable to known exploits and vulnerabilities.Regular patching and updating of the operating system and application software can help mitigate the risk of a successful cyber attack by fixing known vulnerabilities and improving the overall security of the system. It is important to have a defined patch management process that includes regular vulnerability scans, testing of patches in a lab environment before deployment, and a plan for emergency patches when critical vulnerabilities are discovered. Failure to apply patches and updates in a timely manner can leave SCADA systems vulnerable to cyber attacks and put the organization’s critical infrastructure at risk.Our team of experts offers a wide range of solutions to help you monitor and control your industrial processes with ease and efficiency. From system design and implementation to maintenance and support, we provide end-to-end solutions tailored to meet your specific needs.
Our services are designed to maximize uptime, reduce downtime, and enhance productivity while ensuring the highest level of safety and security. Please learn more about our SCADA services and how we can help you optimize your industrial operations.
- Role-Based Access Control
Role-based access control (RBAC) is a security model that can help limit access to SCADA systems to authorized personnel. RBAC allows access to be granted based on the role of the user within the organization, rather than granting access to individual users. This helps to ensure that personnel only have access to the areas they require to perform their duties.For example, an operator may only have access to view and control a specific set of equipment, while an engineer may have access to perform maintenance and modify system configurations. This approach can help limit the risk of unauthorized access and reduce the impact of a potential security breach.
Implementing RBAC requires a well-defined access control policy and a system for assigning roles and managing access privileges. It is also important to regularly review and update access privileges to ensure that they remain appropriate and up-to-date. - Intrusion Detection Systems
Intrusion detection systems (IDS) are an essential component of SCADA system security, as they can detect and prevent cyber attacks by monitoring network traffic and alerting security personnel to potential threats. IDS can help identify abnormal network activity, such as unauthorized access attempts, malware infections, and network vulnerabilities.IDS can be deployed either as a hardware device or as software installed on a server. When IDS detects a potential threat, it can send an alert to security personnel, allowing them to respond quickly and take appropriate actions to prevent or mitigate the impact of the attack. Deploying IDS requires a well-defined security policy and a thorough understanding of the SCADA network architecture. It is also important to regularly review and update IDS policies and configurations to ensure that they remain effective and up-to-date.
By deploying IDS, organizations can proactively detect and prevent cyber attacks, helping to maintain the security and integrity of their SCADA systems.
- Physical Security
Physical security measures are an important aspect of SCADA system security. These measures help prevent unauthorized physical access to SCADA systems, which could result in serious security breaches or operational disruptions. Security cameras, access control systems, and security guards are all effective physical security measures that can be used to protect SCADA systems.Security cameras can be used to monitor access points and other critical areas, providing real-time surveillance and recording footage for review in the event of an incident. Access control systems can restrict access to sensitive areas, ensuring that only authorized personnel are allowed to enter. Security guards can also be deployed to monitor access points and respond to potential security incidents. Deploying physical security measures requires a thorough assessment of the physical security risks and vulnerabilities of the SCADA system, as well as a well-defined security policy and plan for incident response.
By implementing physical security measures, organizations can help protect their SCADA systems from unauthorized physical access, helping to maintain the safety and integrity of their critical infrastructure.
- Employee Training
Employee training is a critical aspect of SCADA system security, as employees play a crucial role in preventing cyber attacks. Employees should receive regular training on how to identify and report suspicious activity, such as phishing emails or unauthorized access attempts.They should also be trained on how to use security measures, such as two-factor authentication and secure password practices, to help protect the SCADA system from unauthorized access. In addition, employees should be trained on how to respond to a cyber attack, including how to report incidents and who to contact in the event of a security breach.
Employee training should be conducted regularly and should be tailored to the specific roles and responsibilities of each employee within the organization. This can help ensure that all employees have the knowledge and skills necessary to effectively prevent and respond to cyber attacks, helping to maintain the security and integrity of the SCADA system.
SCADA systems are critical for controlling and monitoring industrial processes. However, SCADA systems are often targeted by cybercriminals because of their criticality and potential consequences of a successful attack. Protecting SCADA systems from cyber threats is essential to ensure their reliable and secure operation. Implementing appropriate security measures such as secure remote access, network segmentation, regular patching and updating, role-based access control, intrusion detection systems, physical security, and employee training can help prevent cyber attacks and protect industrial control systems.
If you’re looking to improve your knowledge and skills in the field of cybersecurity for SCADA (Supervisory Control and Data Acquisition), you should consider attending our workshop. Our cybersecurity workshop is designed to teach you the fundamental principles of cybersecurity, including how to protect your computer systems and networks from cyber-attacks. The SCADA workshop, on the other hand, will focus on the principles and technologies used in the management and control of industrial processes. Both workshops will offer a hands-on learning experience, allowing you to gain practical knowledge that you can immediately apply in your work.
By attending our workshops, you will not only expand your knowledge and skills but also ensure that you are up-to-date with the latest industry trends and best practices.
Agile MES: The Key to Unlocking Smart Manufacturing Success
MES is a computerized system used in manufacturing operations to track and document the transformation of raw materials into finished goods. An MES system typically manages and monitors work orders, equipment, materials, and personnel on the shop floor. The system provides real-time visibility into production processes, helps optimize manufacturing operations, and improves the overall efficiency of the manufacturing process.
Understanding OEE: The Key to Manufacturing Efficiency
In today’s competitive manufacturing landscape, improving efficiency and productivity is crucial for businesses to remain competitive. One of the key metrics used to measure manufacturing efficiency is OEE or Overall Equipment Effectiveness. In this blog, we will take a closer look at OEE and its importance in manufacturing.
How to Effectively Conduct a Legacy System Integration
Legacy system integration can be a daunting task, but it’s a necessary one for many manufacturers that rely on outdated systems to run their business. Integrating legacy systems with modern technology can improve efficiency, streamline processes, and save time and money. However, it’s important to approach the integration process carefully and methodically to ensure success.
Share on :
Keep On Reading
Subscribe to Our Newsletter
Subscribe to our weekly newsletters to get updates regarding our new production, behind the scene process of our art creation and much more.
After submitting this form you will receive an e-mail with a confirmation link that you must click to complete your request. Detailed information on processing and cancellation can be found in our privacy policy.


